Smartphone Hacking: Android and Beyond
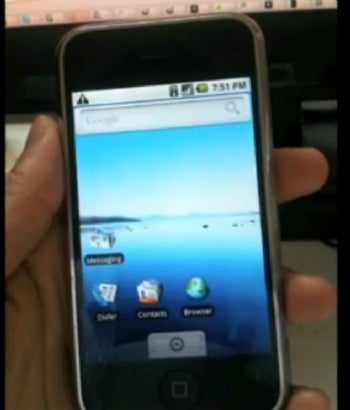
Of all the mind-bending news items that have come out in the last few months, this one was up there on the ridiculous-o-meter: getting an iPhone to run the Android operating system. It's like a Hackintosh in reverse!
If you're looking to jailbreak your iPhone/iPad/iPod Touch but didn't want to use your USB cable, you're in luck. An untethered jailbreak for the iPhone called "Spirit" makes the entire jailbreaking process a lot slicker than having to use your computer to reboot your device running the iPhone 3.1.3 OS.
Overclocking, once the domain of folks trying to eek a few extra MHz out of their CPUs, has spread to the phone hacking community, and you can now overclock your iPhone or iPod Touch.
ReadMore>>